Wireless Network Watcher is a dependable and user-friendly software designed to monitor and analyze network devices within a wireless network. It has evolved into a necessary tool for both home users and IT professionals due to its extensive capabilities and simplicity of use. In this detailed review, we will explore the functionalities and benefits of Wireless Network Watcher, providing you with an in-depth understanding of this powerful network monitoring software.
You May Also Read
- How to Lock Whatsapp Chat
- How to Identify Fake Currency Notes
- How to Connect Any WiFi Without Password
What is Wireless Network Watcher?
In today’s digital world where network security is of utmost importance, monitoring network devices becomes crucial. Wireless Network Watcher, developed by NirSoft, offers a solution to keep track of all devices connected to your wireless network. Whether you want to ensure network security or identify unauthorized access, this software provides valuable insights and tools to achieve these objectives.
How Wireless Network Watcher Works?
Wireless Network Watcher works by scanning the wireless network and capturing information about the devices connected to it. It uses the Address Resolution Protocol (ARP) and the Dynamic Host Configuration Protocol (DHCP) to obtain detailed information about each device, such as IP and MAC addresses, device name, manufacturer, and more. The software constantly monitors the network and updates the device list in real-time, providing an accurate representation of the network’s status.
Key Features of Wireless Network Watcher
Scanning and Monitoring Network Devices
Wireless Network Watcher excels in its ability to scan and monitor network devices efficiently. Upon launching the software, it automatically initiates a scan of the wireless network and displays a list of connected devices. The intuitive interface presents the information in a clear and organized manner, allowing users to quickly identify devices and their corresponding details.
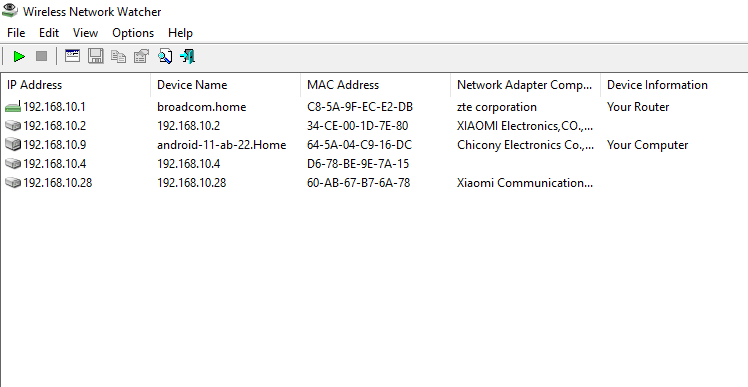
Detecting Unwanted Network Connections
One of the notable features of Wireless Network Watcher is its ability to detect and highlight unwanted network connections. Suspicious or unauthorized devices can be easily identified through the software’s alert system, which flags any unfamiliar or unrecognized devices within the network. This feature enables users to take immediate action and secure their network from potential threats.
Customization Options
Wireless Network Watcher offers customization options to tailor the scanning process according to specific requirements. Users can define scan intervals, exclude certain IP addresses or ranges from scans, and configure alert settings based on their preferences. These customization options enhance the flexibility and usability of the software, accommodating diverse network environments.
Exporting and Saving Results
To maintain a record of network devices and their activities, Wireless Network Watcher allows users to export and save the scan results. Users can export the device list in various formats such as CSV, HTML, XML, or plain text, making it convenient for further analysis or documentation. This feature ensures that users can keep track of network device information and maintain a history of network changes over time.
Compatibility and Ease of Use
Wireless Network Watcher is compatible with Windows operating systems and supports both 32-bit and 64-bit versions. The software boasts a user-friendly interface that requires no technical expertise to navigate. Its intuitive design and straightforward controls make it accessible to users of all levels, from beginners to experienced network administrators.
Benefits of Using Wireless Network Watcher
Network Security Enhancement
With the rise of cyber threats, ensuring the security of your wireless network is paramount. Wireless Network Watcher plays a vital role in enhancing network security by providing real-time visibility into connected devices. By regularly monitoring the network, users can detect and identify any unauthorized or suspicious connections, allowing for prompt action to mitigate potential security breaches.
Identifying Unauthorized Access
Wireless Network Watcher aids in identifying unauthorized access to your wireless network. It alerts users to any devices that are not recognized or have not been granted access, enabling them to identify and address potential security risks promptly. This feature is particularly useful for monitoring network activity and preventing unauthorized users from exploiting network resources.
Monitoring Network Performance
In addition to security aspects, Wireless Network Watcher allows users to monitor the performance of their wireless network. By analyzing the connected devices and their activities, users can gain insights into network traffic, bandwidth usage, and potential bottlenecks. This information assists in optimizing network performance and ensuring a seamless user experience.
Troubleshooting Network Issues
When network connectivity or performance issues arise, Wireless Network Watcher serves as a valuable troubleshooting tool. By providing a comprehensive overview of all connected devices, users can pinpoint potential problematic devices or configurations. This facilitates the identification and resolution of network issues, minimizing downtime and maintaining network stability.
Step-by-Step Guide to Using Wireless Network Watcher
To make the most out of Wireless Network Watcher, follow this step-by-step guide:
Downloading and Installing the Software
Click on the download button and download the portable version of wnetwatcher.
Launching the Application
After downloading, launch Wireless Network Watcher by double-clicking its icon on the desktop .
Scanning for Network Devices
Upon launching, Wireless Network Watcher will automatically initiate a scan of your wireless network. Wait for the scan to complete, which usually takes a few seconds to a few minutes, depending on the network size.
Analyzing the Results
Once the scan is complete, the software will display a list of connected devices along with their details. Review the information to identify authorized devices and detect any suspicious or unfamiliar ones.
Taking Action on Suspicious Connections
If Wireless Network Watcher identifies any suspicious connections, take appropriate action to secure your network. This may involve blocking or removing unauthorized devices, updating network security settings, or seeking further assistance from a network administrator.
Customizing the Scan Options
Wireless Network Watcher allows customization of scan settings. Explore the software’s options to set scan intervals, exclude specific IP addresses or ranges, and configure alerts according to your preferences.
Tips for Maximizing the Use of Wireless Network Watcher
To maximize the benefits of Wireless Network Watcher, consider the following tips:
Regular Scanning and Monitoring
Perform regular scans using Wireless Network Watcher to stay updated on the devices connected to your network. Schedule scans at appropriate intervals to ensure ongoing visibility and security.
Setting Up Alerts
Configure the alert settings in Wireless Network Watcher to receive notifications whenever a new device connects to the network or when suspicious activity is detected. This proactive approach enables prompt action and enhances network security.
Updating the Software
Stay up to date with the latest version of Wireless Network Watcher. Regularly check for software updates and install them to ensure optimal performance and compatibility with your operating system.
Integrating with Other Security Tools
Wireless Network Watcher can be used in conjunction with other security tools and software to create a comprehensive network security solution. Consider integrating it with firewalls, antivirus programs, or intrusion detection systems for a layered approach to network protection.
Conclusion
Wireless Network Watcher is a valuable and efficient network monitoring software that offers numerous benefits to users. From enhancing network security and identifying unauthorized access to monitoring network performance and troubleshooting issues, this software provides comprehensive functionalities in an accessible and user-friendly manner. By following the step-by-step guide and implementing the tips mentioned, users can make the most out of Wireless Network Watcher and ensure the security and performance of their wireless networks.
Is Wireless Network Watcher a free software?
Yes, Wireless Network Watcher is available as freeware, allowing users to download and use it without any cost.
Does Wireless Network Watcher require administrative privileges to scan the network?
Yes, Wireless Network Watcher requires administrative privileges to access and scan the network devices effectively.
Can Wireless Network Watcher be used in large enterprise networks?
While Wireless Network Watcher can be used in small to medium-sized networks, for large enterprise networks, it may be more suitable to consider dedicated network monitoring solutions that offer scalability and advanced features.
Can Wireless Network Watcher detect devices connected to both 2.4GHz and 5GHz networks?
Yes, Wireless Network Watcher can detect and monitor devices connected to both 2.4GHz and 5GHz wireless networks.
Does Wireless Network Watcher require an active internet connection to function?
No, Wireless Network Watcher operates locally and does not require an active internet connection for scanning and monitoring wireless networks.
Is Wireless Network Watcher compatible with all wireless router brands?
Yes, Wireless Network Watcher is compatible with a wide range of wireless router brands, as long as they adhere to standard networking protocols.
Can Wireless Network Watcher be used for network forensics?
While Wireless Network Watcher provides valuable information about connected devices, it is primarily designed for real-time monitoring and network security. For comprehensive network forensics, specialized tools and techniques may be required.



